Certificate templates are imported from their source rather than created in Keyfactor Command, which means there are limited operations that need to be performed in Keyfactor Command in relation to them. Supported actions on the certificate template![]() A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. page include:
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received. page include:
-
Import Templates
The certificate templates in the primary Active Directory forest
 An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. (the forest in which Keyfactor Command is installed) will be imported automatically by the Keyfactor Command configuration wizard during the Keyfactor Command installation if Keyfactor Command is installed on a domain-joined server. The template import option is used for templates from other sources, new templates created or edited after the Keyfactor Command installation, or template import for non-domain-joined Keyfactor Command servers.
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers. (the forest in which Keyfactor Command is installed) will be imported automatically by the Keyfactor Command configuration wizard during the Keyfactor Command installation if Keyfactor Command is installed on a domain-joined server. The template import option is used for templates from other sources, new templates created or edited after the Keyfactor Command installation, or template import for non-domain-joined Keyfactor Command servers. -
Configure System-Wide Settings
The global settings option allows you to configure regular expressions, certificate subject defaults and policies that apply to all enrollments unless overridden by template-level settings.
-
Edit Template Options
Although templates are imported from their source, there are multiple Keyfactor Command-specific settings that can be configured on the templates to allow them to be used within the product.
-
View Certificates for a Template
The view certificates option takes you to the certificate search interface with the query field populated by the selected template.
 Importing Certificate Templates
Importing Certificate Templates
You only need to import templates if you have EJBCA CAs, Microsoft CAs in forests other than the forest in which Keyfactor Command was installed, are running Keyfactor Command on a non-domain-joined server, or have added a new template or changed the name or key size![]() The key size or key length is the number of bits in a key used by a cryptographic algorithm. of a template after it has been imported into Keyfactor Command and don't want to wait for the automated import process or have not configured the automated process (see Certificate Templates).
The key size or key length is the number of bits in a key used by a cryptographic algorithm. of a template after it has been imported into Keyfactor Command and don't want to wait for the automated import process or have not configured the automated process (see Certificate Templates).
To import certificate templates:
- In the Management Portal, browse to Locations > Certificate Templates.
- On the Certificate Templates page, click Import Templates.
-
In the Select Configuration Tenant
 A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. dialog, select a configuration tenant in the dropdown.Tip: Previous versions of Keyfactor Command referred to the Configuration Tenant as the Template Forest.
A grouping of CAs. The Microsoft concept of forests is not used in EJBCA so to accommodate the new EJBCA functionality, and to avoid confusion, the term forest needed to be renamed. The new name is configuration tenant. For EJBCA, there would be one configuration tenant per EJBCA server install. For Microsoft, there would be one per forest. Note that configuration tenants cannot be mixed, so Microsoft and EJBCA cannot exist on the same configuration tenant. dialog, select a configuration tenant in the dropdown.Tip: Previous versions of Keyfactor Command referred to the Configuration Tenant as the Template Forest.If you have a forest in a two-way trusted relationship with the forest in which Keyfactor Command is installed or have configured a Microsoft CA
 A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. with the Use Explicit Credentials option or an EJBCA CA, the configuration tenant for this CA will appear in the dropdown. Import once for each configuration tenant containing templates that you want to import. The import process may take several seconds.
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. with the Use Explicit Credentials option or an EJBCA CA, the configuration tenant for this CA will appear in the dropdown. Import once for each configuration tenant containing templates that you want to import. The import process may take several seconds.
- Short Name: <end entity profile name>_<certificate profile name>
- Display Name: <end entity profile name> (<certificate profile name>)
Only certificate profiles configured as available in a given end entity profile will be imported as templates associated with the given end entity profile name.
 Configuring System-Wide Settings
Configuring System-Wide Settings
System-wide settings apply to all enrollments done through Keyfactor Command unless they are overridden by template-specific settings (see Enrollment Regexes Tab, Enrollment Defaults Tab, and Policies Tab). Although system-wide settings are configured on the templates page, they also apply to enrollments done without a template (e.g. standalone CAs).
To configure system-wide options:
- In the Keyfactor Command Management Portal, browse to Locations > Certificate Templates.
- On the Certificate Templates page, click System-Wide Settings at the top of the grid.
- When you open the system-wide settings, you will see three tabs. Configure the system-wide setting information with the appropriate data using the following instructions.
- Click Save to save the system-wide settings. Click Back to return to the certificate templates page.
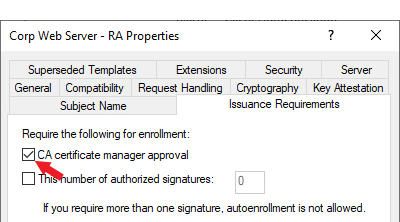
Regular expressions for enrollment are used to validate that the data entered in the certificate subject fields meets certain criteria.
To configure a system-wide regular expression:
- On the Enrollment RegExes tab, double-click a subject part row in the grid, right-click the row and choose Edit from the right-click menu, or highlight the row in the grid and click Edit at the top of the grid.
- On the Enrollment RegEx dialog, in the RegEx field, enter a regular expression against which to validate the subject part. See Regular Expressions for examples.
- In the Error field, enter an error message to be displayed to the user in the enrollment pages of the Keyfactor Command Management Portal or as a response to an enrollment API
 A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. request when the subject part referenced in the CSR
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command. request when the subject part referenced in the CSR A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. or entered for a PFX
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. or entered for a PFX A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. does not match the regular expression defined for the subject part field. Note that the error message already includes the subject part followed by a colon (e.g. Organization: or Invalid O provided: depending on the interface). Your custom message follows this.
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers. does not match the regular expression defined for the subject part field. Note that the error message already includes the subject part followed by a colon (e.g. Organization: or Invalid O provided: depending on the interface). Your custom message follows this. - Click Save to save the regular expression.
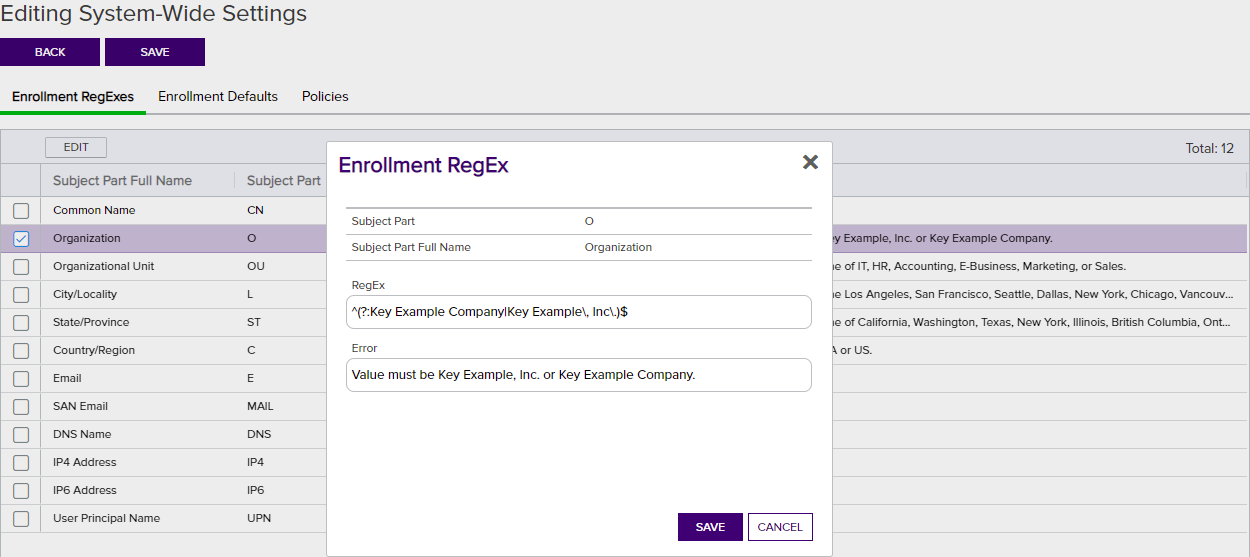
Figure 224: Configure System-Wide Enrollment Regular Expressions
This will disallow entry of any data in the SAN field and thus prevent users from submitting the certificate request with this SAN.
Enrollment defaults allow you to define default values for select certificate subject parts that will auto-populate on the PFX enrollment and CSR generation pages in the Keyfactor Command Management Portal.
To configure a system-wide enrollment default:
- On the Enrollment Defaults tab, double-click a subject part row in the enrollment defaults grid, right-click the row and choose Edit from the right-click menu, or highlight the row in the grid and click Edit at the top of the grid.
-
On the Enrollment Default dialog, in the Value field, enter a value to auto-populate in the PFX enrollment and CSR generation pages of the Keyfactor Command Management Portal. During PFX enrollment or CSR generation, the user can accept the value or modify it; it is not enforced.
- Click Save to save the default.
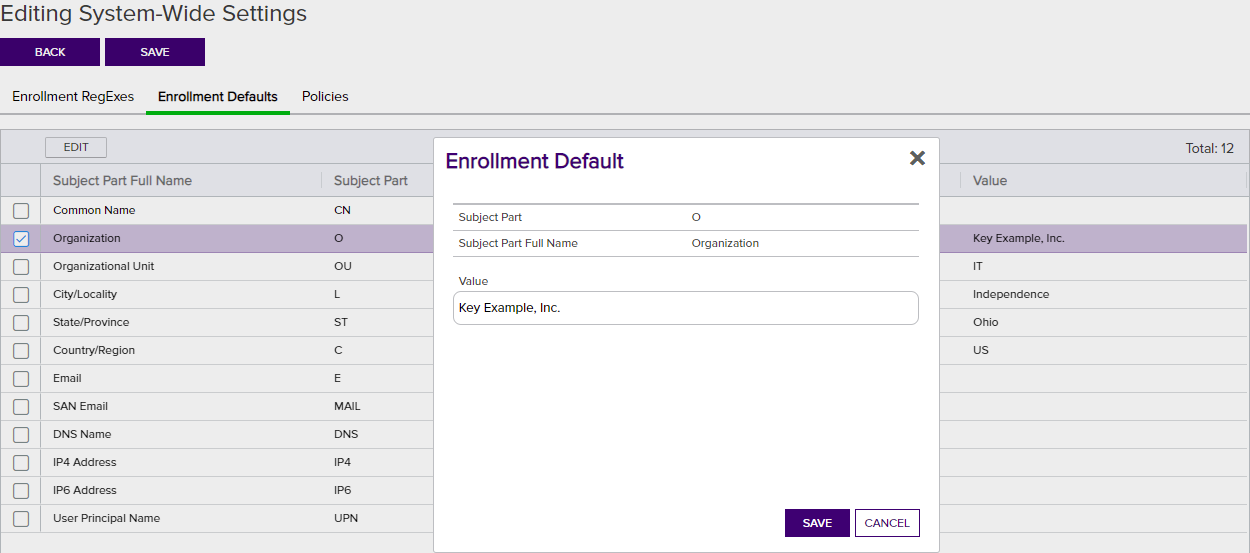
Figure 225: Configure System-Wide Enrollment Defaults
Policies for templates cover the following settings:
Enrollment Policies
-
Allow Wildcards
Enable this option to allow certificates to be created containing wildcards (e.g. *.keyexample.com). The default is enabled.
-
Enable this option to allow public keys to be reused on certificate renewals. The default is enabled.
-
Enforce RFC 2818 Compliance
Enable this option to force certificate enrollments made through Keyfactor Command to include at least one DNS
 The Domain Name System is a service that translates names into IP addresses. SAN. In the Keyfactor Command Management Portal, this causes the CN
The Domain Name System is a service that translates names into IP addresses. SAN. In the Keyfactor Command Management Portal, this causes the CN A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). entered in PFX enrollment to automatically be replicated as a DNS Name SAN, which will be set to Read Only. For CSR enrollment, if the CSR does not have a SAN that matches the CN, one will automatically be added to the certificate if this is set. The default is disabled.Tip: For CA gateways, some cloud providers will automatically include SANs without you needing to enable the Enforce RFC 2818 Compliance option. Some cloud providers won’t support submission of a SAN that matches the CN (which is the default when you enable the RFC 2818 option). Keyfactor recommends disabling this option for CA gateways.
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). entered in PFX enrollment to automatically be replicated as a DNS Name SAN, which will be set to Read Only. For CSR enrollment, if the CSR does not have a SAN that matches the CN, one will automatically be added to the certificate if this is set. The default is disabled.Tip: For CA gateways, some cloud providers will automatically include SANs without you needing to enable the Enforce RFC 2818 Compliance option. Some cloud providers won’t support submission of a SAN that matches the CN (which is the default when you enable the RFC 2818 option). Keyfactor recommends disabling this option for CA gateways.
Supported Key Types
-
RSA Key Sizes
A list of RSA key sizes that are valid for enrollment through Keyfactor Command. If a key size is not in this list, enrollment will not be supported for requests specifying that key size. To change the selected values, in the dropdown uncheck any values you do not wish to support. The default values are:
2048, 3072, 4096 -
A list of elliptic curve algorithms that are valid for enrollment through Keyfactor Command. To change the selected values, in the dropdown uncheck any values you do not wish to support. The default values are:
P-256/prime256v1/secp256r1, P-384/secp384r1, P-521/secp521r1 -
Allow Ed448 / Allow Ed25519
Set global template values for allowing Ed448 and Ed25519 keys. Templates that utilize Ed448 or Ed25519 key types can be imported into Keyfactor Command. These key types are only available with EJBCA CAs. Default is disabled.
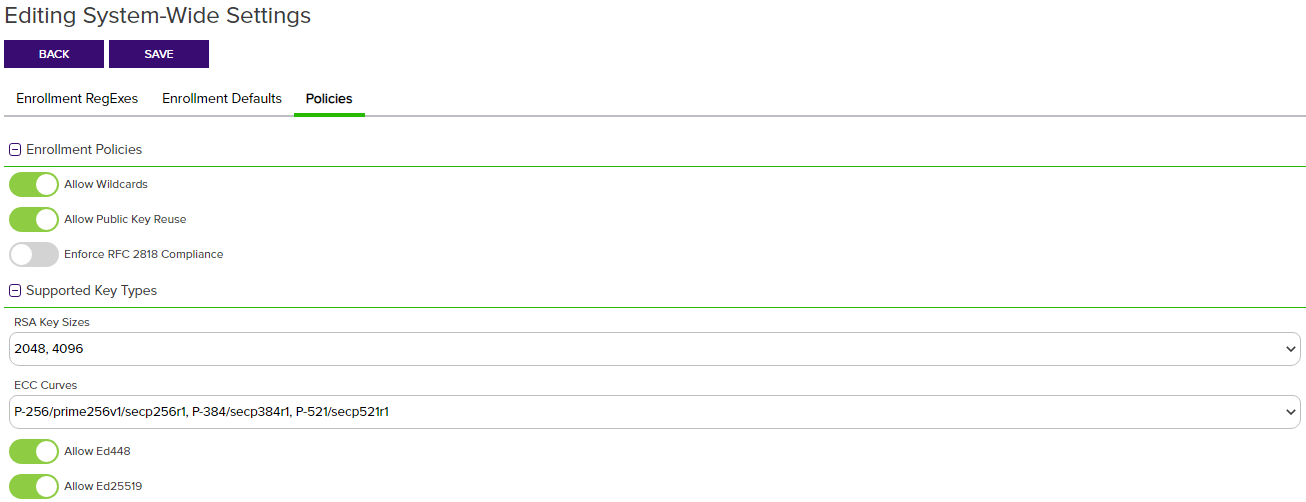
Figure 226: Configure System-Wide Policies
 Configuring Template Options
Configuring Template Options
The options configured in templates relate to how they appear and function for PFX and CSR enrollment in the Management Portal.
To configure template options:
- In the Keyfactor Command Management Portal, browse to Locations > Certificate Templates.
- On the Certificate Templates page, double-click the template, right-click the template and choose Edit from the right-click menu, or highlight the row in the template grid and click Edit at the top of the grid.
- When you open the certificate template for editing, you will see several tabs. Complete the template information with the appropriate data using the following instructions.
- Click Save to save the changes to the template record. Click Back to return to the main certificate templates page without saving changes.
Details
The information in the Details section is for reference and cannot be edited. This includes:
-
Template Short Name—The common name
 A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). of the template. This name typically does not contain spaces.
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). of the template. This name typically does not contain spaces. -
Template Display Name—The display name of the template.
-
Key Size—The minimum supported key size of the template.
-
OID—For a Microsoft certificate template, the object ID of the template retrieved from Active Directory. For an EJBCA certificate template, this field is generated within Keyfactor Command as an object identifier
 Object identifiers or OIDs are a standardized system for identifying any object, concept, or "thing" with a globally unambiguous persistent name., but does not follow official OID
Object identifiers or OIDs are a standardized system for identifying any object, concept, or "thing" with a globally unambiguous persistent name., but does not follow official OID Object identifiers or OIDs are a standardized system for identifying any object, concept, or "thing" with a globally unambiguous persistent name. conventions.
Object identifiers or OIDs are a standardized system for identifying any object, concept, or "thing" with a globally unambiguous persistent name. conventions. -
Curve—For ECC templates, the elliptic curve algorithm defined for the certificate template.
Key Types and Sizes
The Key Types and Sizes section displays all the configured key types information for the template.
Friendly Name
In the Friendly Name section, enter a Friendly Name, if desired. Template friendly names, if configured, appear in template selection dropdowns in place of the template short names. This can be useful in environments where the template short names are long or not very human readable. This setting is not required to enable enrollment or configure private key![]() Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. retention.
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. retention.
Allowed Enrollment Types
In the Allowed Enrollment Types section, click the toggle buttons to enable the options for CSR Enrollment, PFX Enrollment and/or CSR Generation as desired. Enabling these options causes the template to appear in dropdowns in the corresponding section of the Management Portal. In the case of CSR Enrollment and PFX Enrollment, the templates only appear in dropdowns on the enrollment pages if they are available for enrollment from a CA also configured for enrollment within Keyfactor Command (see Adding or Modifying a CA Record).
If you wish to use One-Click Renewal for certificates, the Allow One-Click Renewals option must be enabled in both the templates and CAs to which you want One-Click Renewal to apply (see Certificate Template Operations and Adding or Modifying a CA Record).
Private Key Retention
In the Private Key Retention section, click the toggle button to enable Private Key Retention, if desired, and select the ![]() retention type in the dropdown. Enter the number of days, weeks, months, or years to keep the encrypted private key stored in the Keyfactor Command database based on the type selected, then select the desired time frame (Day(s), Week(s), Month(s), or Year(s)). You will not have the option to choose a retention timeframe if you choose Indefinite.
retention type in the dropdown. Enter the number of days, weeks, months, or years to keep the encrypted private key stored in the Keyfactor Command database based on the type selected, then select the desired time frame (Day(s), Week(s), Month(s), or Year(s)). You will not have the option to choose a retention timeframe if you choose Indefinite.
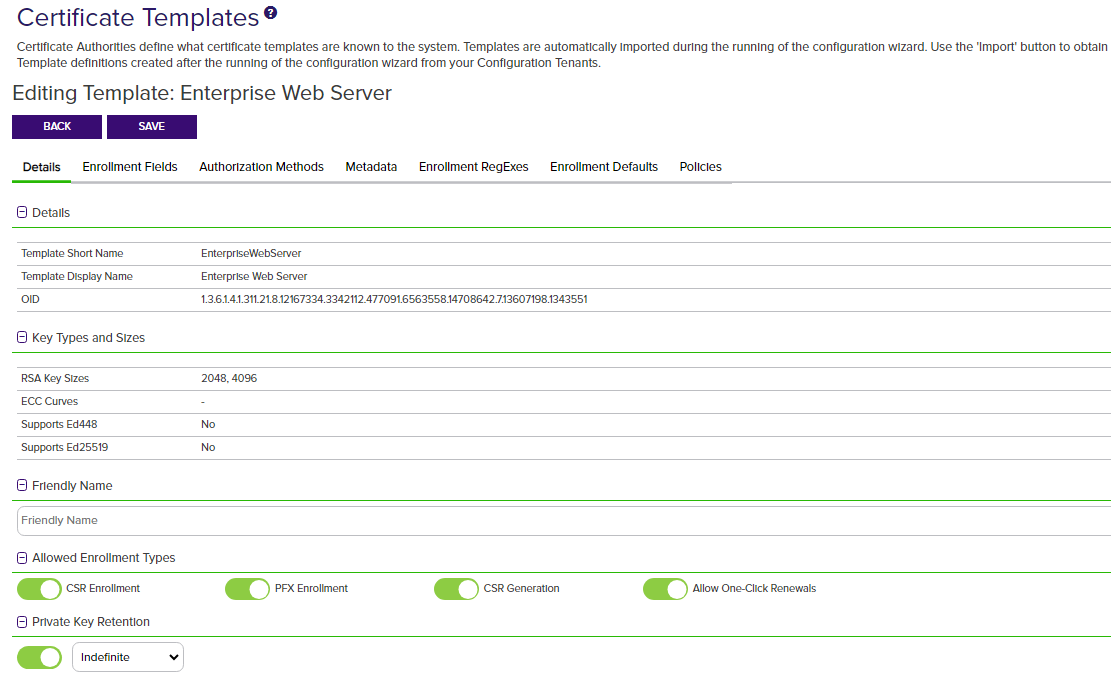
Figure 228: Certificate Template: Details Tab for a Microsoft Template
On the Enrollment Fields tab, you can add custom enrollment fields. These are configured on a per-template basis to allow you to submit custom fields with CSR enrollments and PFX enrollments to supply custom request attributes to the CA during the enrollment process. This functionality offers such benefits as:
- Preventing users from requesting invalid certificates, based on your specific certificate requirements per template.
- Providing additional information to the CA with the request.
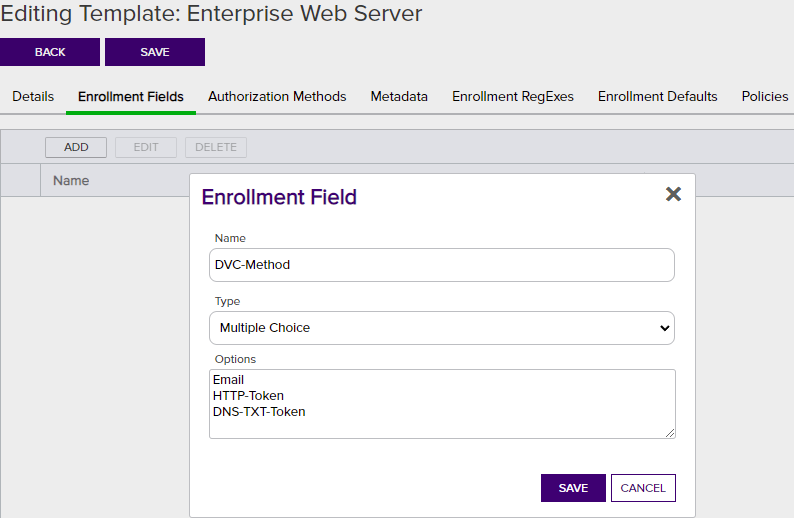
Figure 229: Configure Template: Enrollment Fields Tab
Once created on the template, these values are shown in Keyfactor Command on the PFX and CSR enrollment pages in the Additional Enrollment Fields section. The fields are mandatory during enrollment. The data will appear on the CA / Issued Certificates attribute tab for certificates enrolled with a template configured with Keyfactor Command enrollment fields.
On the Enrollment Fields tab you can add, edit and delete enrollment fields.
To add a new enrollment field:
- On the Enrollment Fields tab of the selected template click Add. If there are existing fields configured they will appear in a list on this tab.
- Enter a Field Name for the new custom field. This name will appear on the enrollment pages.
- Select a Parameter Type. The options are:
- String: A free-form data entry field.
- Multiple Choice: Provides a list of acceptable values for the field. A text box will open up below this choice for you to enter the list of acceptable values. Add each value on a separate line. Click OK to close the box.
- Click Save to save and close the add window.
The Restrict Allowed Requesters option is used to select Keyfactor Command security roles that a user must belong to in order to successfully enroll for certificates in Keyfactor Command using this template. This is typically used for EJBCA templates and Microsoft templates that are not in the local Active Directory forest, since in these cases, Keyfactor Command cannot make use of the access control model of the CA itself to determine which users can enroll for certificates; this setting replaces that functionality. This setting is similar to setting request certificates for the selected security roles at the template level on a Microsoft CA. For multi-forest environments, this setting should be used on any templates from forests other than the Keyfactor Command forest that will be used for enrollment regardless of the type of trust between the forests, including two-way trusts.
On the Authorization Methods tab you can add, edit and delete allowed requesters.
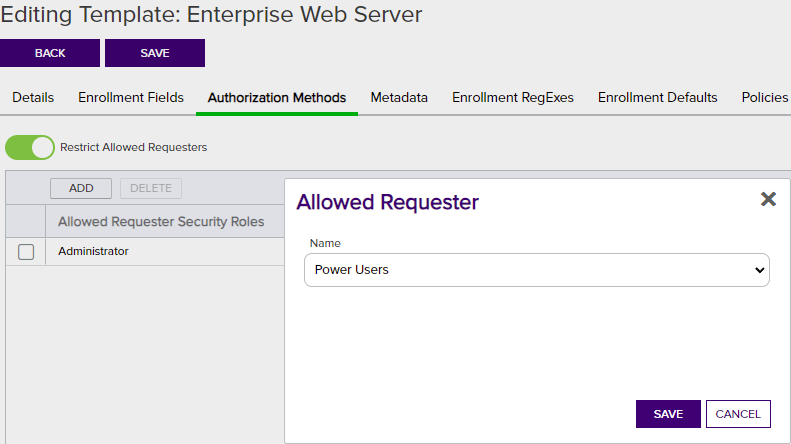
Figure 230: Certificate Template: Authorization Methods Tab
To add a new allowed requester, click to toggle the Restrict Allowed Requesters button and:
- On the Authorization Methods tab of the selected template click Add. If there are existing requesters configured, they will appear in a list on this tab.
- In the Security Role dropdown, select a Keyfactor Command security role (see Security Roles and Claims) to grant enrollment permissions on the template.
- Click Save to save and close the add window.
From the Metadata tab you can:
-
View the metadata field settings for that specific template.
-
Configure how (or whether) the metadata fields will appear during enrollment for that specific template.
System-Wide Settings
System-wide metadata fields are defined in System Settings (see Certificate Metadata) and displayed here.
Template Settings
Once the system-wide metadata has been defined, the Enrollment Handling setting can be configured on a template-specific basis, potentially overriding a system-wide required, hidden or optional setting for that metadata field on that template, causing only the set of fields configured for the template to appear on the PFX and CSR enrollment pages when the template is selected, and determining if they are required or optional.
A default value for a metadata field can also be configured that is different from, and overrides, the default value entered for the system-wide metadata field. For string metadata fields, a regular expression validation and error message can also be configured on a template-specific basis. The order in which the metadata fields appear can be changed globally (see Sorting Metadata Fields).

Figure 231: Certificate Template: Metadata Tab
The Metadata grid columns can be sorted by clicking the column heading (except Default Value). The columns are:
-
Name: The name of the metadata field.
-
Data Type: The metadata field type: String, Integer, Date, Boolean, Multiple Choice, Email, or Big Text.
-
Enrollment Handling: The handling of the metadata field during enrollment: Optional, Required or Hidden.
-
Default Value: The default value during enrollment, if there is one, will be displayed.
-
Uses System-Wide Settings: Displays Yes if system-wide settings are in effect for this template, or No if template-specifc settings are in effect.
To configure metadata fields for a template:
- On the Metadata tab, double-click a row in the metadata grid, right-click the row and choose Edit from the right-click menu, or highlight the row in the grid and click Edit at the top of the grid.
- In the Metadata dialog in the System-Wide Settings section, review the existing system-wide settings for the metadata field.
- In the Template Settings section, click to toggle the Override system-wide settings button. Configure the template-level settings for the metadata field. The available fields will vary depending on the type of the metadata field and may include:
Choose the Enrollment Options for this template by selecting the appropriate radio button:
Optional: The metadata field will appear during enrollment with this template, but it will not be required to complete enrollment.
Required: This field will be required in order to complete enrollment with this template.
Hidden: This field will not be displayed during enrollment with this template.
- Set the Default Value if desired. If no default value is desired, the field may be left blank. For Multiple Choice type metadata fields, this field will appear as a dropdown where you can select from the existing values configured for the metadata field.
- If desired, set a RegEx Message and RegEx Validation string specific to the template used to validate the value upon enrollment entry, and any error message to display if the entry does not match the regex definition. For more information, see Adding or Modifying a Metadata Field. This option is supported for string type metadata fields.
- Click Save on the Metadata dialog to save changes for each metadata field.
Enrollment Regexes can be applied at either the template-specifc level or system-wide level. Template-level regular expressions are used to validate that the certificate subject data entered on the CSR enrollment, CSR generation, and PFX enrollment pages meets certain criteria. Template-level regular expressions differ from system-wide regular expressions (see Configuring System-Wide Settings) as they apply on a per-template basis, rather than system-wide. In the case of a conflict in a regular expression between system-wide and template-level definitions, the template-level regular expression takes precedence.
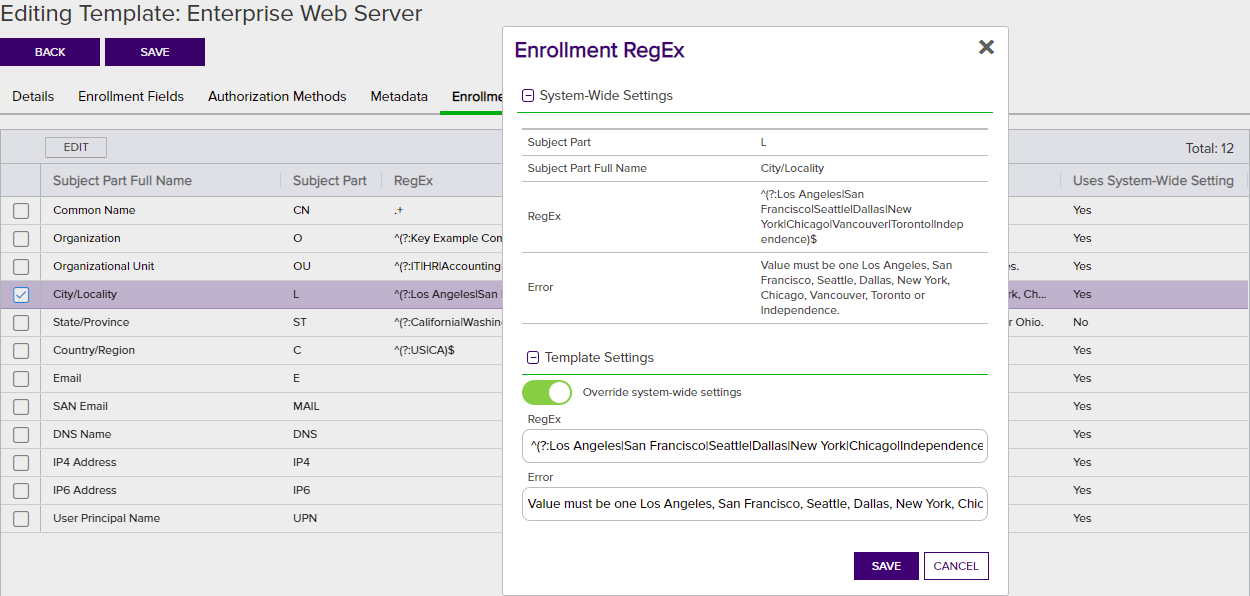
Figure 232: Certificate Template: Enrollment RegExesTab
The Enrollment Regexes grid columns can be sorted by clicking the column heading (except Regex and Error). The columns are:
-
Subject Part Full Name: The descriptive name of the certificate subject part (e.g. Common Name).
-
Subject Part: The code for the certificate subject information part. For instance, CN=Common Name.
-
RegEx: The regular expression to apply to the subject part.
-
Error: The error message to display (upon Save when enrolling), when the entry does not meet the specified criteria.
-
Uses System-Wide Settings: Displays Yes if system-wide settings are in effect for this template, or No if template-specifc settings are in effect.
To configure template regular expression fields for a template:
- On the Template Regexes tab, double-click a row in the regular expression grid, right-click the row and choose Edit from the right-click menu, or highlight the row in the grid and click Edit at the top of the grid.
- In the Enrollment RegEx dialog in the System-Wide Settings section, review the existing system-wide settings for the subject part.
- In the Template Settings section, click to toggle the Override system-wide settings button. Enter a regular expression in the RegEx field. See Regular Expressions for examples.
- In the Error field enter the error message to display during enrollment if the data entered for the subject part does not meet the validation rule.
-
Click Save on the Enrollment RegEx dialog to save each template-level regular expression.
The regular expressions will be applied at the time of enrollment. Entries which do not match the regular expression requirements will be flagged with an error message during enrollment entry when you click Enroll (or Generate for CSR generation).
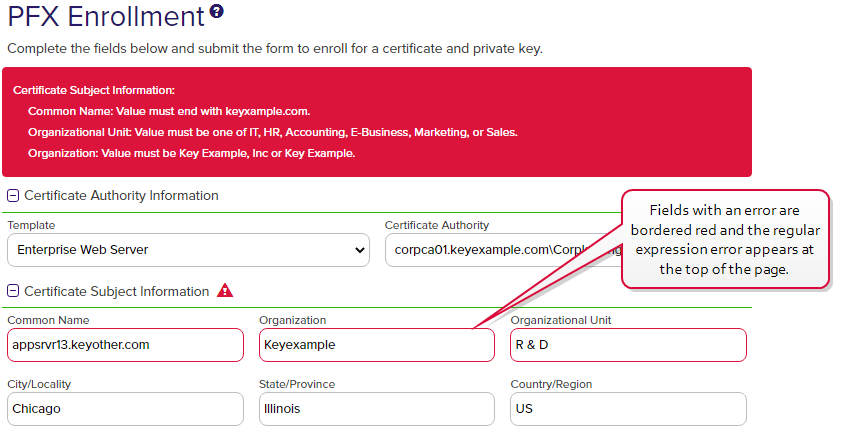
Figure 233: Certificate Template: Template Regular Expression Error on Enrollment
This will disallow entry of any data in the SAN field and thus prevent users from submitting the certificate request with this SAN.
Template-level enrollment defaults allow you to define default values for certificate subject parts that will auto-populate on the PFX enrollment and CSR generation pages in the Keyfactor Command Management Portal. Template-level default values differ from system-wide default values (see Configuring System-Wide Settings) as they apply on a per-template basis, rather than system-wide. In the case of a conflict in a default value between system-wide and template-level definitions, the template-level default values takes precedence.
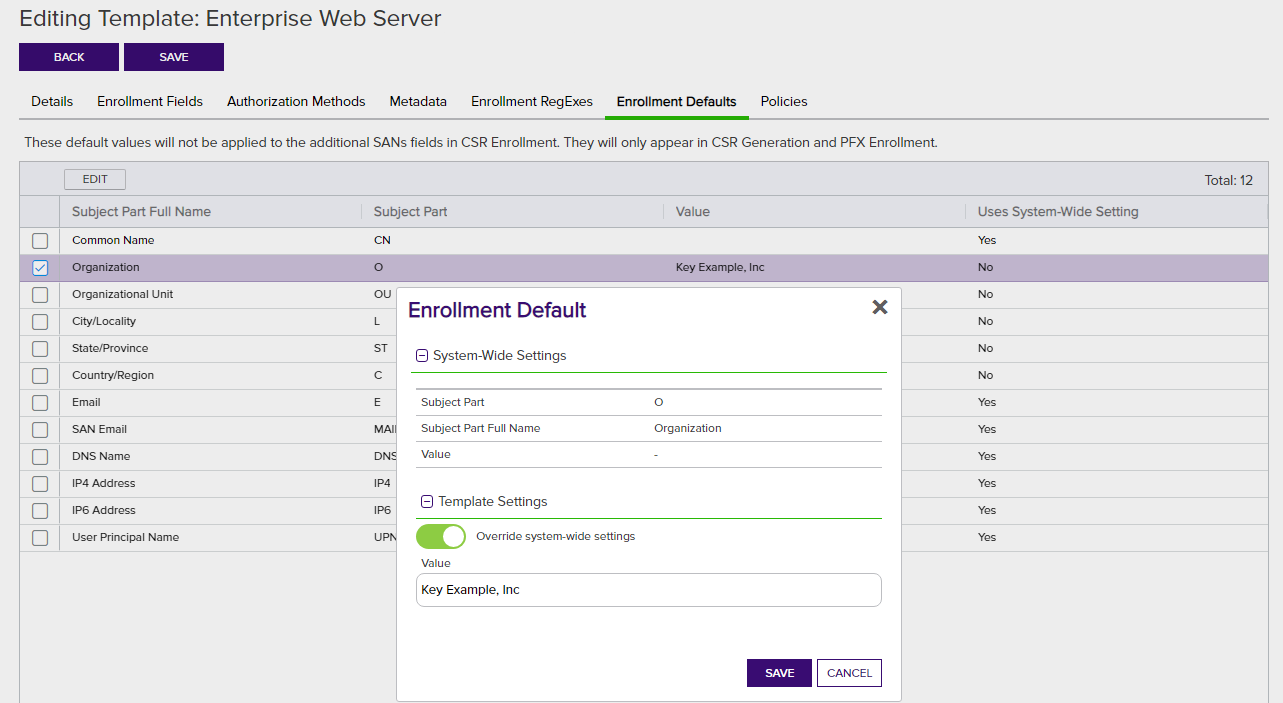
Figure 234: Certificate Template: Enrollment Defaults Tab
The Enrollment Defaults grid columns can be sorted by clicking the column heading (except Value). The columns are:
-
Subject Part Full Name: The descriptive name of the certificate subject part (e.g. Common Name).
-
Subject Part: The code for the certificate subject information part. For instance, CN=Common Name.
-
Value: The default value to apply to the subject part.
-
Uses System-Wide Settings: Displays Yes if system-wide settings are in effect for this template, or No if template-specific settings are in effect.
To configure template-level default values for a template:
- On the Enrollment Defaults tab, double-click a row in the defaults grid, right-click the row and choose Edit from the right-click menu, or highlight the row in the grid and click Edit at the top of the grid.
- In the Enrollment Default dialog in the System-Wide Settings section, review the existing system-wide default value for the subject part.
- In the Template Settings section, click to toggle the Override system-wide settings button. Enter a template-level default value for the subject part in the Value field.
- Click Save on the Enrollment Default dialog to save each template-level default.
The Policies Tab allows you to set template-level policy definitions which take precedence over system-wide settings (see Configuring System-Wide Settings).
Enrollment Policies
The Enrollment Policies section displays the System-Wide Setting (Yes or No) for each of the template enrollment policies and allows you to Override System-Wide Setting for the specific template. Enabling Override System-Wide Setting will cause the system setting is to be disregarded and allow you to enable or disable the setting for that policy on the template. Override System-Wide Setting does not automatically set the policy to the opposite, the selection on the policy (enabled/disabled) will supersede any other settings.
-
Allow Wildcards
Enable this option to allow certificates to be created containing wildcards (e.g. *.keyexample.com) using this template.
-
Allow Public Key Reuse
Enable this option to allow private keys to be reused on certificate renewals made using this template.
-
Enforce RFC 2818 Compliance
Enable this option to force certificate enrollments made through Keyfactor Command for this template to include at least one DNS SAN. In the Keyfactor Command Management Portal, this causes the CN entered in PFX enrollment to automatically be replicated as a SAN, which the user can either change or accept. For CSR enrollment, if the CSR does not have a SAN that matches the CN, one will automatically be added to the certificate if this is set.
Tip: For CA gateways, some cloud providers will automatically include SANs without you needing to enable the Enforce RFC 2818 Compliance option. Some cloud providers won’t support submission of a SAN that matches the CN (which is the default when you enable the RFC 2818 option). Keyfactor recommends disabling this option for CA gateways.
Supported Key Types
The Supported Key Types section displays the System-Wide Setting (value or Yes/No) for the supported key type![]() The key type identifies the type of key to create when creating a symmetric or asymmetric key. It references the signing algorithm and often key size (e.g. AES-256, RSA-2048, Ed25519). and allows you to Override System-Wide Setting for the specific template. Enabling Override System-Wide Setting will cause the system-wide setting to be disregarded, enable the settings field, and allow you to select the setting for that policy on the template. Override System-Wide Setting does not automatically set the policy to the opposite, the selection on the policy (values or enabled/disabled) will supersede any other settings.
The key type identifies the type of key to create when creating a symmetric or asymmetric key. It references the signing algorithm and often key size (e.g. AES-256, RSA-2048, Ed25519). and allows you to Override System-Wide Setting for the specific template. Enabling Override System-Wide Setting will cause the system-wide setting to be disregarded, enable the settings field, and allow you to select the setting for that policy on the template. Override System-Wide Setting does not automatically set the policy to the opposite, the selection on the policy (values or enabled/disabled) will supersede any other settings.
When configuring template-level policies for key information, only algorithms, sizes, and curves supported for the template by the CA will appear as options for configuration.
Depending on the template selected, one or more of these settings will be available for configuration:
A list of RSA key sizes that are valid for enrollment through Keyfactor Command for this template. If a key size is not in this list, enrollment will not be supported for requests specifying that key size. To change the selected values, in the dropdown check any values you wish to support. The values supported by Keyfactor Command are: 2048, 3072, 4096, 6144, 8192, and 16384. Only values that are valid for the template on the CA will appear as available for selection.
A list of elliptic curve algorithms that are valid for enrollment through Keyfactor Command for this template. To change the selected values, in the dropdown check any values you wish to support. The values supported by Keyfactor Command are: P-256/prime256v1/secp256r1, P-384/secp384r1, and P-521/secp521r1. Only values that are valid for the template on the CA will appear as available for selection.
Enable or disable support for Ed448 or Ed25519 keys on the template.
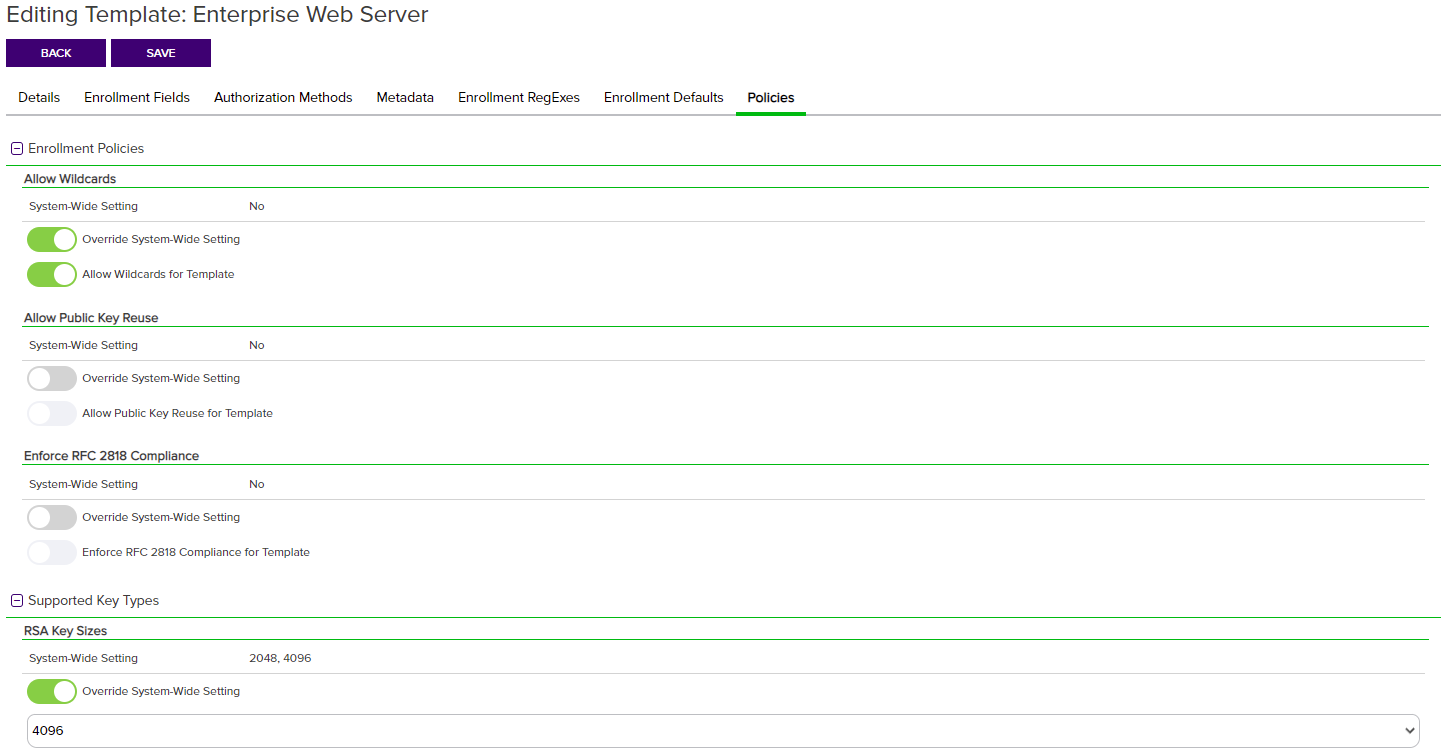
Figure 235: Certificate Template: Policies Tab
For enrollments done through Keyfactor Command for either Microsoft or EJBCA CAs, use Keyfactor Command private key retention (see Details Tab).
 Viewing Template Certificates
Viewing Template Certificates
To view the certificates in the Keyfactor Command database for a given template, highlight the template in the grid and click View Certificates at the top of the grid or right-click the template and choose View Certificates from the right-click menu. This will take you to the certificate search page with the query field populated by the selected template (see Certificate Search Page). You can save the search as a certificate collection![]() The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports). at that point if desired (see Saving Search Criteria as a Collection).
The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports). at that point if desired (see Saving Search Criteria as a Collection).